Nordvpn Review
Nordvpn introduction
Nordvpn: shopify Email marketing
NordVPN Review is a leading Virtual Private Network (VPN) service provider, established in 2012 by Tom Okman and Eimantas Sabaliauskas. The company is headquartered in Panama, a jurisdiction known for its strong privacy laws and absence of mandatory data retention requirements.
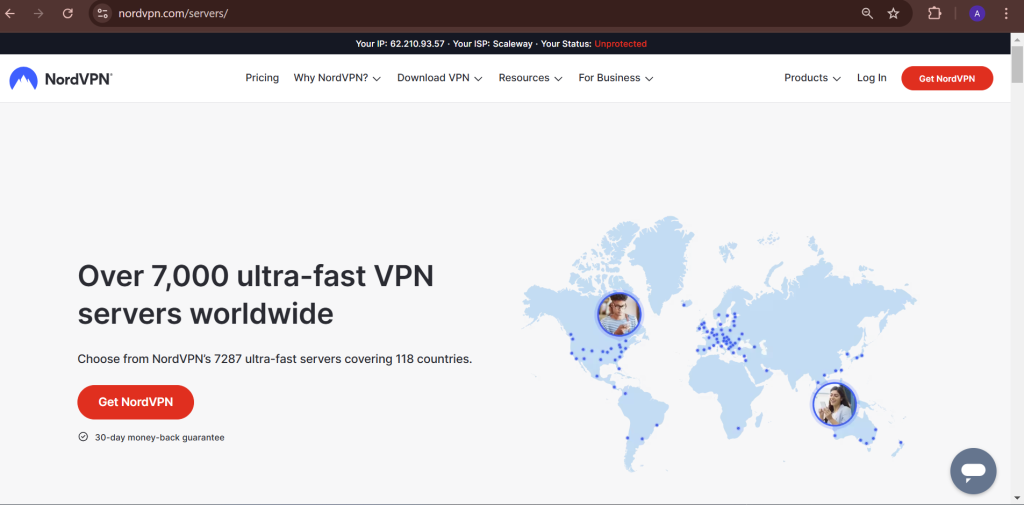
With a vast network of over 7,000 servers across 113 countries, NordVPN offers users fast and reliable connections worldwide
Get 50% off 3 months or a free Trial Nordvpn
Pricing & Plans
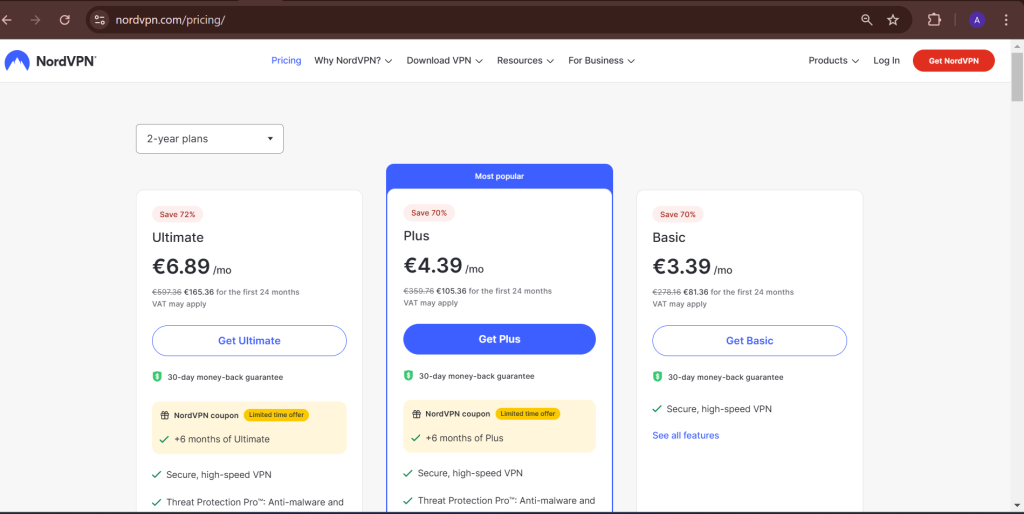
When it comes to pricing, NordVPN offers flexible plans designed to suit different budgets and needs. Whether you’re looking for a short-term solution or a long-term subscription, NordVPN provides a variety of options, each with its own benefits.
NordVPN Subscription Plans
NordVPN offers three main pricing tiers:
- 1-Month Plan: Ideal for those who need a short-term VPN solution, priced at $11.95 per month.
- 1-Year Plan: A more affordable option, costing $4.99 per month, billed annually at $59.00.
- 2-Year Plan: The most cost-effective choice, priced at $3.99 per month, billed at $95.75 for two years.
The longer your subscription, the greater the discount, making the 2-year plan the best deal if you’re looking for long-term protection.
NordVPN Money-Back Guarantee
If you’re unsure about committing, NordVPN offers a 30-day money-back guarantee. This means you can try the service risk-free for a month and receive a full refund if you’re not satisfied with the service. This policy makes NordVPN a low-risk option for those new to VPNs or hesitant about long-term commitments.
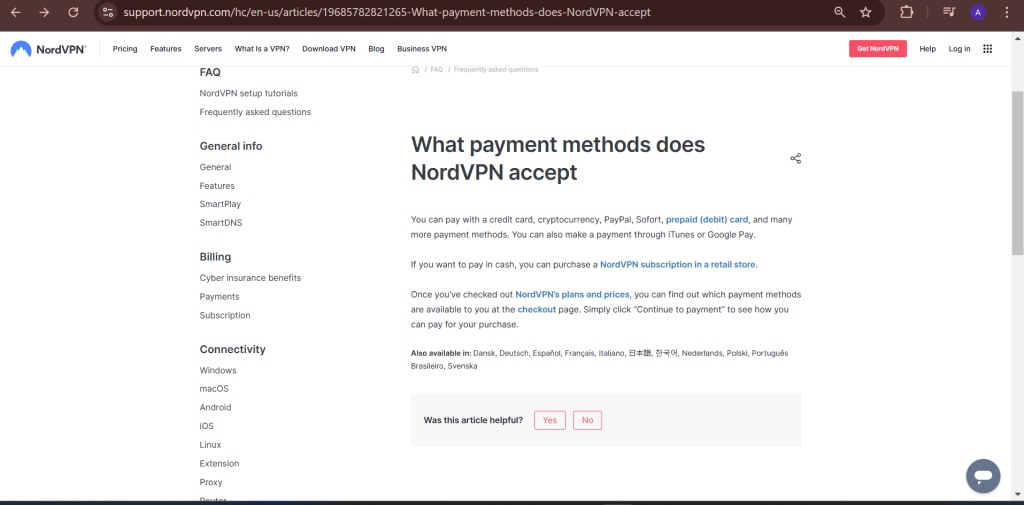
Payment Options
NordVPN supports various payment methods, including credit cards, PayPal, and even cryptocurrencies like Bitcoin for added anonymity. This makes it easy for users to choose the most convenient and private payment method for their subscription.
Discounts & Special Offers
Occasionally, NordVPN offers special deals and seasonal discounts. Keep an eye out for promotions, especially around holidays, as these often provide significant savings on long-term plans.
With its competitive pricing and flexible plans, NordVPN ensures you get great value for your money while enjoying top-tier security and privacy features.
Security & Encryption
NordVPN is one of the most secure VPN services available, offering top-tier encryption and advanced security features to protect user data. Whether you’re browsing, streaming, or handling sensitive information, NordVPN ensures your online activities remain private and secure.
AES-256 Encryption – Military-Grade Security
NordVPN uses AES-256 encryption, the industry-standard encryption protocol trusted by governments, cybersecurity experts, and financial institutions. This ensures that even if your data were intercepted, it would be virtually impossible to decrypt.
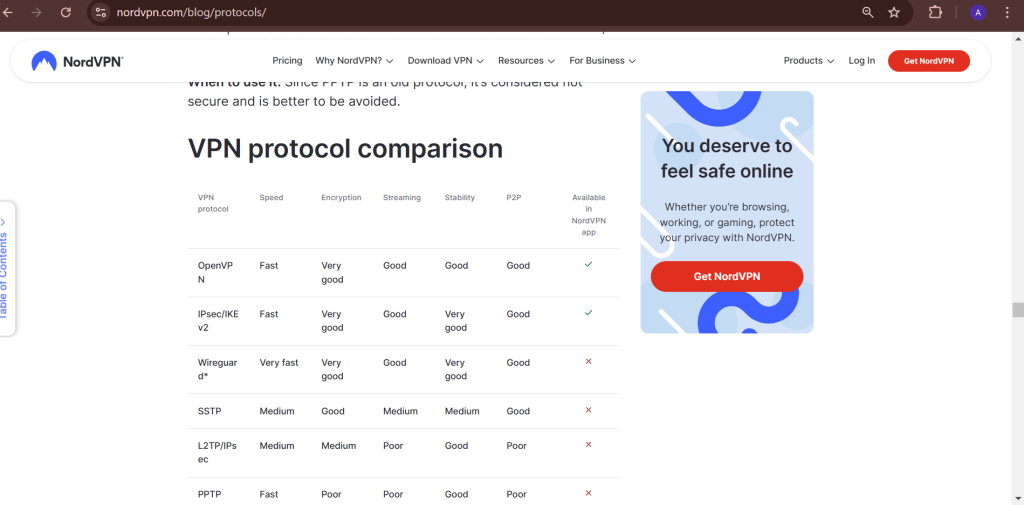
Secure VPN Protocols
NordVPN supports multiple protocols to balance security and speed:
- NordLynx (WireGuard-based): A fast, lightweight, and secure protocol.
- OpenVPN: A widely used open-source protocol offering strong security.
- IKEv2/IPSec: Ideal for mobile users, ensuring a stable and secure connection.
Advanced Security Features
Beyond encryption, NordVPN includes additional tools to enhance security:
- Double VPN: Encrypts your traffic twice by routing it through two servers.
- Onion Over VPN: Adds an extra layer of privacy by combining NordVPN with the Tor network.
- Kill Switch: Automatically disconnects the internet if the VPN drops, preventing data leaks.
Threat Protection & Cybersecurity Tools
NordVPN also provides Threat Protection, which blocks malware, trackers, and phishing attempts, adding an extra layer of security even when you’re not connected to the VPN.
With NordVPN powerful encryption and security features, users can browse the internet with confidence, knowing their data is protected from hackers, surveillance, and cyber threats.
Speed & Performance
NordVPN is known for delivering fast and reliable VPN connections, making it an excellent choice for streaming, gaming, and everyday browsing. With a vast server network and advanced VPN protocols, NordVPN ensures minimal speed loss while maintaining strong security.
High-Speed Servers Worldwide
NordVPN operates 5,000+ servers in 60+ countries, ensuring that users can always connect to a fast and stable server near their location. The closer the server, the better the speed and performance.
NordLynx – The Fastest VPN Protocol
NordVPN uses NordLynx, a VPN protocol based on WireGuard, which offers:
- Faster connection speeds compared to older protocols like OpenVPN.
- Lower latency, making it ideal for gaming and streaming.
- Improved efficiency, reducing the impact on device performance.
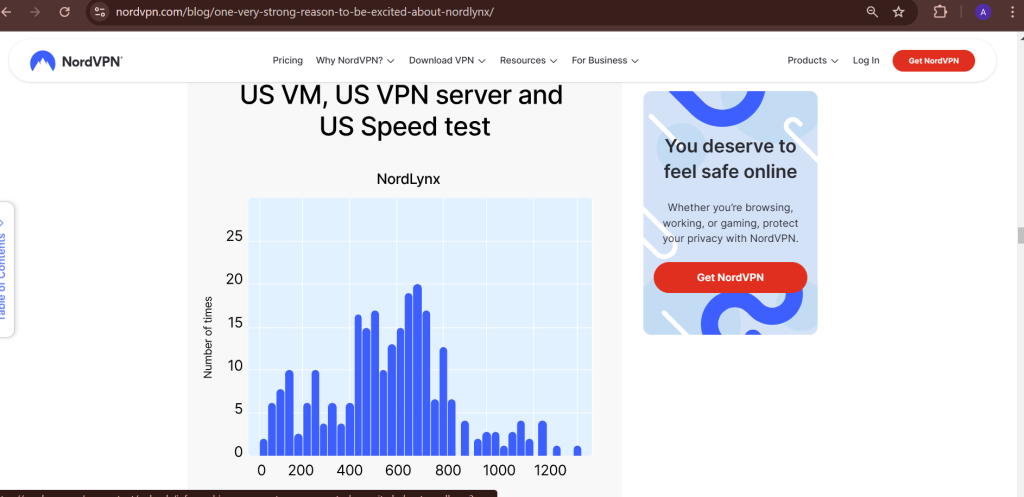
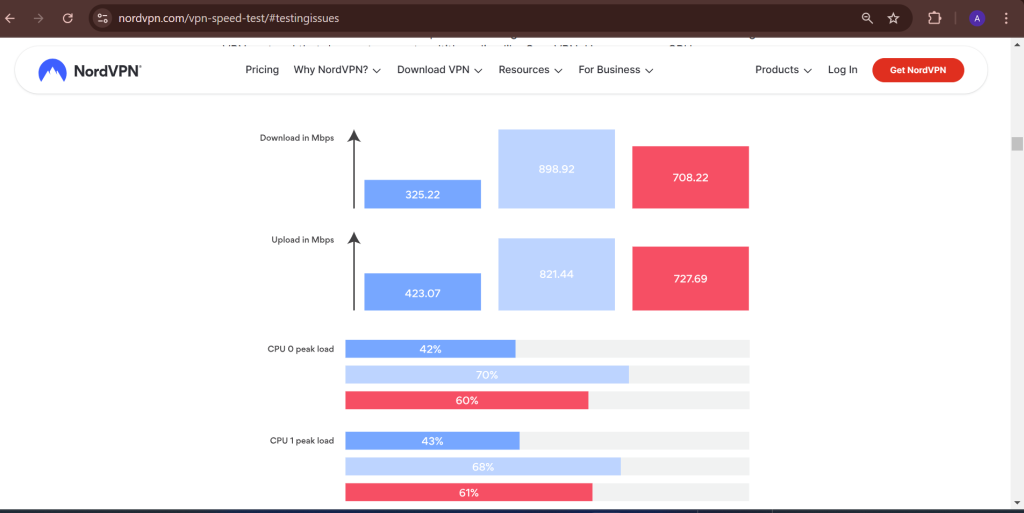
Speed Test Results
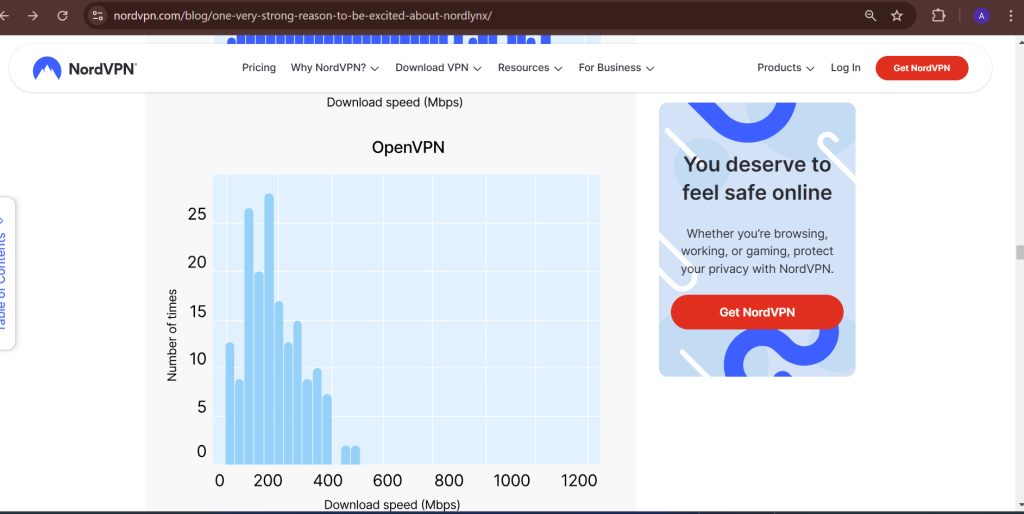
Independent speed tests show that Nordvpn consistently delivers high download and upload speeds, even when connected to distant servers. Factors like server load, encryption overhead, and network congestion can impact performance, but Nordvpn optimizes its servers to minimize slowdowns.
Streaming Without Buffering
NordVPN is optimized for streaming, allowing users to watch Netflix, YouTube, Hulu, and other platforms in HD and 4K quality without buffering. Its SmartPlay feature ensures seamless access to geo-restricted content.
Lag-Free Gaming & Low Latency
For gamers, NordVPN provides:
- Low-ping servers for lag-free online gaming.
- DDoS protection to prevent attacks while gaming.
- Fast connections for downloading and updating games quickly.
Final Verdict on Nordvpn Speed & Performance
Thanks to its optimized servers, NordLynx protocol, and extensive global network, NordVPN offers impressive speed and performance, making it one of the best VPNs for streaming, gaming, and everyday browsing.
Here’s a well-structured and informative content piece on Server Network & Locations with suggestions on where images would be useful:
A strong server network with strategically placed locations is essential for fast, reliable, and secure online experiences. Whether you’re streaming, gaming, or browsing, the right server infrastructure ensures seamless performance and low latency.
What Is a Server Network?
Server Network & Locations
A server network refers to a group of interconnected servers spread across different locations worldwide. These servers store, manage, and process data to deliver fast and secure connections to users.
Why Server Locations Matter
The closer a server is to the user, the faster the connection. Server locations impact:
- Speed & Latency – Nearby servers reduce delays.
- Access to Content – Some content is region-restricted; more locations mean better access.
- Security & Privacy – Distributed servers add redundancy and protection.
- Speed & Latency – Nearby servers reduce delays.
- Access to Content – Some content is region-restricted; more locations mean better access.
- Security & Privacy – Distributed servers add redundancy and protection.
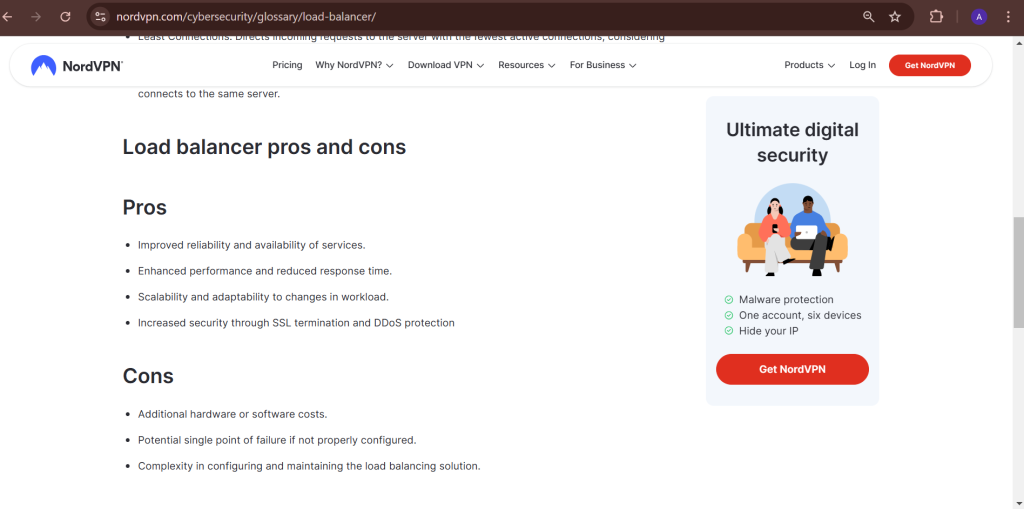
How Server Networks Improve Performance
A well-distributed server network enhances performance through:
- Load Balancing – Traffic is evenly distributed across servers to prevent overload.
- Redundancy & Reliability – Multiple servers ensure uptime even if one goes down.
- Optimized Routing – Data is sent through the fastest and most efficient path.
Choosing a Server Network for Your Needs
When selecting a service with a global server network, consider:
- Number of Locations – More servers mean better speed and access.
- Server Quality – High-performance hardware ensures reliability.
- Privacy Policies – Look for secure, no-log servers for better privacy.
![Best VPN Service Checklist [2025] NordVPN](https://gayrguide.com/wp-content/uploads/2025/02/Screenshot-2025-02-20-165736-1024x502.png)
Conclusion
A well-structured server network and locations ensure faster speeds, better security, and global accessibility. Whether for personal use or business, choosing a provider with a robust network will enhance your overall online experience.
In today’s digital landscape, safeguarding your online privacy is more crucial than ever. A fundamental aspect of this protection is understanding and choosing services that adhere to a strict no-logs policy.
Privacy & No-Logs Policy
What Is a No-Logs Policy?
A no-logs policy is a commitment by a service provider, particularly Virtual Private Network (VPN) services, to refrain from collecting or storing any information about your online activities. This means that:
- Browsing History: The websites you visit are not recorded.
- Connection Timestamps: The times you connect or disconnect are not logged.
- Data Usage: The amount of data transmitted is not tracked.
By not retaining such data, these providers ensure that there is no information available that could be used to trace your online actions back to you.
Adding an image here of a shield or lock symbolizing privacy would visually reinforce the concept.
Why Is a No-Logs Policy Important?
The significance of a no-logs policy lies in its ability to:
- Enhance Privacy: Without logs, there’s no trail of your online behavior.
- Ensure Anonymity: Even if compelled, the provider has no data to share.
- Build Trust: Users can feel confident that their information remains confidential.
An infographic illustrating data flow with and without logging can help clarify this point.
How Do Providers Implement No-Logs Policies?
Reputable providers take several measures to enforce their no-logs policies:
- Independent Audits: Engaging third-party firms to verify their practices.
- Jurisdictional Advantage: Operating in countries with strong privacy laws.
- Minimal Data Collection: Only gathering information essential for service maintenance.
For instance, NordVPN, based in Panama—a country without mandatory data retention laws—has undergone multiple independent audits to confirm its adherence to a strict no-logs policy. citeturn0search2
Similarly, Proton VPN, headquartered in Switzerland, operates under a strict no-logs policy, ensuring that it does not collect, store, or track any information about users’ online activities.
A world map highlighting countries with strong privacy protections can provide geographical context.
Choosing the Right No-Logs Service
When selecting a service that promises a no-logs policy, consider the following:
- Third-Party Verification: Ensure the provider has undergone independent audits.
- Jurisdiction: Opt for services based in privacy-friendly countries.
- Transparency: Look for clear, accessible privacy policies.
A checklist graphic summarizing these points can serve as a quick reference.
Conclusion
A robust no-logs policy is a cornerstone of online privacy, ensuring that your digital footprint remains invisible. By choosing services committed to this standard, you can navigate the internet with greater confidence and security.
An image of a person browsing securely on a device can personalize and conclude the discussion effectively.
Customer Support & Reliability
In today’s competitive market, exceptional customer support and unwavering reliability are pivotal in fostering customer loyalty and trust. Businesses that prioritize these elements not only enhance customer satisfaction but also distinguish themselves from competitors.
The Importance of Customer Support
Effective customer support serves as the frontline of a company’s interaction with its clientele. Key benefits include:
- Building Trust: Prompt and helpful responses demonstrate a company’s commitment to its customers.
- Encouraging Loyalty: Positive support experiences increase the likelihood of repeat business.
- Gathering Feedback: Direct interactions provide valuable insights into customer needs and areas for improvement.
Strategies for Enhancing Customer Support
To elevate customer support, consider implementing the following best practices:
- Empower Employees: Equip support teams with the authority and tools to resolve issues efficiently, fostering a sense of ownership and accountability. citeturn0search0
- Manage Expectations: Clearly communicate service capabilities and timelines to prevent misunderstandings and build trust. citeturn0search0
- Continuous Training: Regularly update staff on product knowledge and customer service skills to ensure they provide accurate and effective assistance.
- Leverage Technology: Utilize customer relationship management (CRM) systems to track interactions and personalize support.
An infographic depicting these strategies can serve as a quick reference guide for businesses aiming to improve their customer support.
Ensuring Service Reliability
Reliability in service delivery is achieved through:
- Consistent Performance: Adhering to promised service standards to build customer confidence.
- Proactive Maintenance: Regular system checks and updates to prevent issues before they affect customers.
- Transparent Communication: Informing customers promptly about any service changes or disruptions.
A flowchart illustrating the process of maintaining service reliability can provide clarity on the steps involved.
Case Study: First Direct’s Commitment to Customer Service
First Direct, a UK-based bank, exemplifies excellence in customer support and reliability. With 87% of its workforce dedicated to customer service, the bank maintains an impressive 39-second average call waiting time, significantly shorter than the industry average. This dedication has solidified its reputation for outstanding customer interactions.
Including a logo or image of First Direct’s customer service center can highlight their commitment to excellence.
Conclusion
Prioritizing robust customer support and ensuring reliability are essential components for business success. By adopting best practices and learning from industry leaders, companies can enhance customer satisfaction and foster long-term loyalty.
Additional Features & Extras
In the realm of Virtual Private Networks (VPNs), beyond the standard offerings of encryption and IP masking, many providers offer a suite of additional features and extras to enhance user experience, security, and accessibility. Understanding these can help you choose a VPN that best fits your needs.
1. Multi-Device Support
Modern users often operate multiple devices. Leading VPNs offer support for simultaneous connections:
- Unlimited Connections: Some services, like Surf shark, allow unlimited simultaneous connections, enabling you to secure all your devices under a single account. citeturn0search12
- Multiple Devices: Others, such as Nordvpn, permit up to six devices to connect simultaneously, balancing security and performance. citeturn0search11
Visual Aid: An image depicting various devices (laptops, smartphones, tablets) connected securely can illustrate this feature.
2. Specialty Servers
To cater to specific user requirements, VPNs provide specialized servers:
- P2P Servers: Optimized for peer-to-peer sharing, ensuring fast and secure torrenting experiences.
- Double VPN: Routes your traffic through two servers, adding an extra layer of encryption for heightened security.
- Onion Over VPN: Combines VPN encryption with the Tor network, offering maximum anonymity.
Visual Aid: A flowchart demonstrating data passing through multiple servers can clarify the Double VPN process.
3. Ad and Malware Blocking
Enhancing online safety, some VPNs incorporate features to block unwanted content:
- Ad Blockers: Prevent intrusive advertisements, leading to a cleaner browsing experience.
- Malware Protection: Guards against malicious websites and downloads, safeguarding your device from potential threats.
Visual Aid: An image of a shield intercepting ads and malware icons can symbolize this protective feature.
4. Split Tunneling
This feature offers flexibility in routing your internet traffic:
- Selective Routing: Allows you to choose which applications or websites utilize the VPN connection and which access the internet directly, optimizing performance and access. citeturn0search1
Visual Aid: A diagram showing two pathways—one encrypted (VPN) and one direct (regular internet)—can illustrate split tunneling.
5. Dedicated IP Addresses
For users requiring a consistent IP address:
- Unique IP Assignment: Provides a static IP address exclusive to you, beneficial for accessing sensitive networks or online banking without triggering security alerts.
Visual Aid: An illustration of a user connected to a unique IP address, distinct from shared IPs, can depict this concept.
6. Obfuscation and Camouflage Modes
To bypass network restrictions and censorship:
- Obfuscated Servers: Conceal the fact that you’re using a VPN, enabling access in regions with strict internet policies.
- Camouflage Mode: Ensures your VPN usage remains undetectable, even by your internet service provider. citeturn 0search 12
Visual Aid: An image representing stealth, such as a masked figure blending into the background, can symbolize obfuscation features.
7. GPS Spoofing
Particularly useful for mobile users:
- Location Masking: Alters your device’s GPS coordinates to match the VPN server location, enhancing privacy and access to location-specific services. citeturn 0search 12
Visual Aid: A map with a pin dropped in a different location than the user’s actual position can illustrate GPS spoofing.
Conclusion
Exploring these additional features and extras can significantly enhance your VPN experience, tailoring it to your specific needs for security, privacy, and convenience. When selecting a VPN, consider which of these features align with your online activities to make an informed choice.
Torrenting & P2P Support
Peer-to-Peer (P2P) file sharing, commonly known as torrenting, is a popular method for distributing and downloading large files efficiently. However, engaging in torrenting without proper security measures can expose users to various risks, including legal issues and cyber threats. Utilizing a Virtual Private Network (VPN) with robust torrenting and P2P support is essential to ensure privacy, security, and optimal performance during file sharing activities.
Understanding Torrenting and P2P File Sharing
Torrenting involves downloading files from multiple sources simultaneously, which accelerates the download process. This decentralized approach relies on P2P networks, where users (peers) share pieces of files with each other without relying on a central server.
Adding an image here of a simplified diagram illustrating P2P file sharing can help visualize the process.
Why Use a VPN for Torrenting?
While torrenting itself is a legitimate technology, it is often associated with sharing copyrighted material, leading to potential legal concerns. Moreover, ISPs may monitor and throttle P2P traffic, resulting in reduced speeds. A VPN addresses these issues by:
- Hiding Your IP Address: Conceals your real IP, making your online activities anonymous.
- Encrypting Data Traffic: Protects your data from being monitored or intercepted.
- Bypassing Throttling: Prevents ISPs from slowing down your connection based on your activities.
An image depicting a secure shield over a torrent download icon can emphasize the protection a VPN offers.
Key Features of VPNs Supporting Torrenting
When selecting a VPN for torrenting, consider the following features:
- P2P-Optimized Servers: Servers specifically configured for efficient and secure P2P file sharing.
- No-Logs Policy: Ensures the VPN provider does not record your online activities.
- Kill Switch: Automatically disconnects your device from the internet if the VPN connection drops, preventing data leaks.
- High-Speed Connections: Essential for quick downloads and smooth streaming.
A comparison table highlighting these features across different VPN providers can aid in decision-making.
Top VPNs for Torrenting
Here are some reputable VPNs known for their strong torrenting and P2P support:
- NordVPN: Offers P2P-configured servers and double encryption for added security, making it a top choice for torrenting. citeturn0search3
- Surfshark: Provides unlimited simultaneous connections and robust security features, ensuring anonymity during torrenting activities.
- Private Internet Access (PIA): Boasts a vast server network with high data privacy standards, supporting P2P traffic across all servers. citeturn0search4
- Windscribe: Supports P2P traffic on all its free servers, securing it via AES-256 encryption and secure tunneling protocols.
Including logos or icons of these VPN services can provide visual recognition and assist users in identifying them.
Setting Up a VPN for Torrenting
To safely engage in torrenting using a VPN:
- Choose a VPN Service: Select a provider that supports P2P traffic and has a strict no-logs policy.
- Install the VPN Application: Download and install the app on your device.
- Connect to a P2P Server: Within the VPN app, select a server optimized for P2P sharing.
- Enable the Kill Switch: Activate this feature to prevent data leaks.
- Start Torrenting: Open your torrent client and proceed with your downloads securely.
A step-by-step infographic can visually guide users through this setup process.
Conclusion
Engaging in torrenting and P2P file sharing carries inherent risks, but with the right VPN, you can protect your privacy, maintain security, and enjoy optimal performance. By selecting a VPN that offers dedicated P2P support, a no-logs policy, and robust security features, you can torrent with confidence and peace of mind.